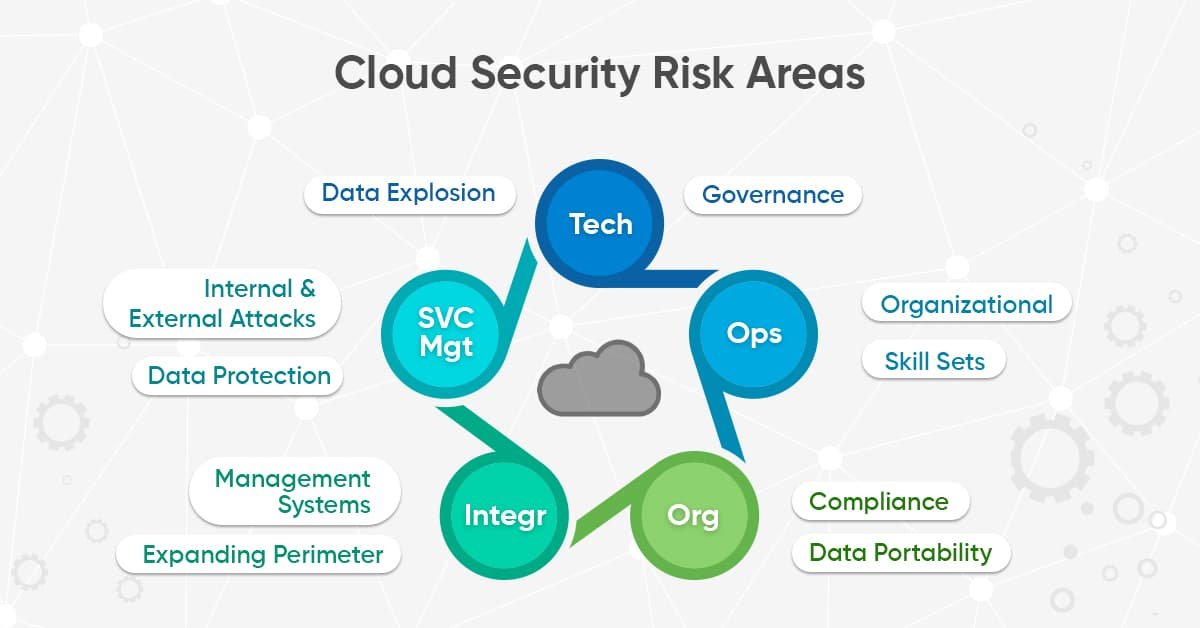
Cloud computing is no longer a luxury — it’s a business necessity. But as more companies move to platforms like AWS, Azure, and Google Cloud, security missteps can quickly turn cost-saving technology into a costly disaster.
From data breaches to downtime, poor cloud security practices can lead to financial loss, legal liability, and long-term brand damage.
Here are the 5 most common cloud security mistakes businesses make — and how to avoid them.
🔐 1. Leaving Storage Buckets Public
One of the most frequent and dangerous mistakes is leaving cloud storage buckets (like AWS S3 or Google Cloud Storage) public by default.
⚠️ The Risk:
- Anyone with the link can view, download, or even edit your files
- Sensitive data exposure (customer records, credentials, source code)
✅ The Fix:
- Always configure private access settings
- Use IAM policies to control user permissions
- Enable logging and version control for monitoring
🔐 2. Weak or Misconfigured Access Controls
Cloud platforms give you granular control — but many teams skip proper role-based access management (RBAC), leading to overly broad privileges.
⚠️ The Risk:
- Insider threats or accidental data deletion
- Unauthorized access to critical systems
✅ The Fix:
- Use the Principle of Least Privilege (PoLP)
- Implement multi-factor authentication (MFA)
- Regularly audit and rotate credentials and API keys
🔐 3. Ignoring Shared Responsibility
Many assume the cloud provider handles all security — but that’s a myth.
⚠️ The Risk:
- Cloud vendors secure the infrastructure, but you are responsible for:
- Data encryption
- App security
- Access management
✅ The Fix:
- Understand your provider’s shared responsibility model
- Implement your own layers of security for apps, networks, and endpoints
🔐 4. Lack of Data Encryption
Unencrypted data in transit or at rest is a golden ticket for attackers.
⚠️ The Risk:
- Man-in-the-middle attacks
- Compliance violations (GDPR, HIPAA, PCI-DSS)
✅ The Fix:
- Enable TLS/SSL for all communications
- Encrypt sensitive data at rest using AES-256 or stronger
- Use KMS (Key Management Services) for secure encryption key storage
🔐 5. No Ongoing Monitoring or Incident Response Plan
Once deployed, many businesses “set it and forget it” — leaving vulnerabilities unnoticed.
⚠️ The Risk:
- Delayed detection of breaches or attacks
- Inability to respond effectively under pressure
✅ The Fix:
- Use cloud-native security monitoring tools like AWS CloudTrail, Azure Monitor, or Google Cloud Logging
- Create and test an incident response plan
- Automate alerts for suspicious activity
🧠 Bonus Tip: Use Security Benchmarks
Align your infrastructure with industry-recognized benchmarks like:
- CIS Benchmarks
- NIST Cybersecurity Framework
- ISO/IEC 27001
These provide a structured path toward building a secure and compliant cloud environment.
🏁 Final Thoughts
Cloud security isn’t just about protecting your business from hackers — it’s about protecting your customers, data, and reputation.
In 2025, cloud threats are evolving faster than ever. Don’t let small mistakes turn into big losses.
At C5K IT, we help businesses secure their cloud infrastructure through:
- Architecture audits
- Real-time monitoring
- Compliance consulting
- Disaster recovery planning
👉 Get a Free Cloud Security Assessment and make sure your systems are protected — before it’s too late.





Leave a Reply